Cybersecurity and the 2019 European Parliament Elections One Year to Go. And Counting.

With one year to go before elections to the European Parliament in May 2019, Europe’s political parties are staring down a path littered with potential efforts to disrupt the vote. History tells us that these threats are real and deserve serious attention and that preventative measures need to be taken now. At the same time, experience shows that this is not being done. That’s where IRI, NDI and Harvard’s Belfer Center come in.
Government officials and civic leaders across Europe have been focused on cyberattacks on major democratic institutions at least since the widely publicized intrusion into the systems of the German Bundestag in 2015, attributed by German intelligence officials to Russian hackers. Concern mounted into the major election year of 2017, in which both The Netherlands and Norway decided to do their national vote counts on paper in case electronic systems were to be disrupted, French presidential candidate Emanuel Macron’s campaign was the ‘victim of a massive and coordinated hack,’ and Germany scrambled to protect its systems after attacks on think tanks closely associated with the country’s two major parties.
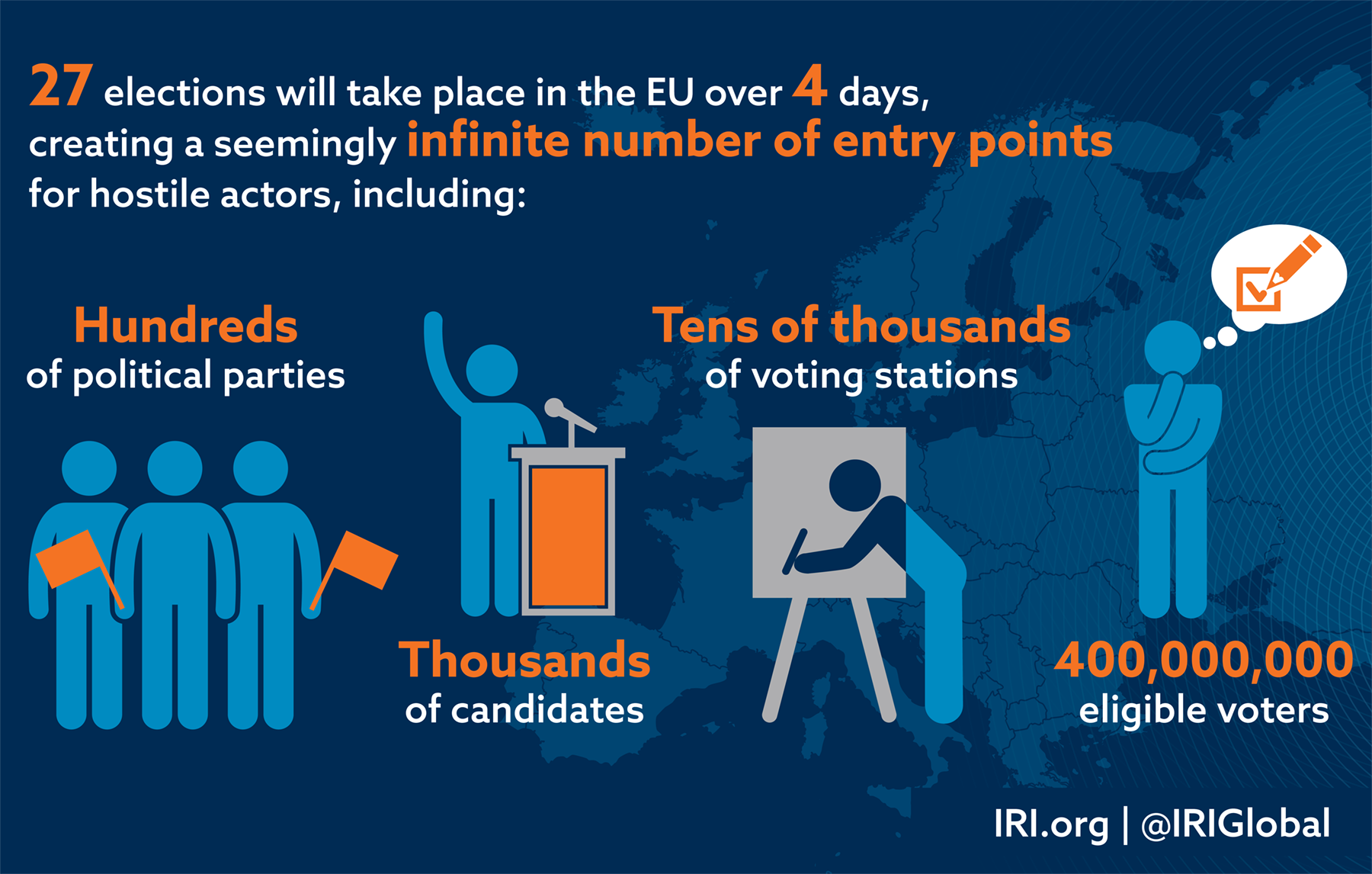
These were all, of course, national elections. But in many ways, the 2019 European Parliament elections provide an even more enticing target for hostile influence campaigns than any single national ballot. A series of 27 individual, decentralized and nationally managed elections taking place across the entirety of the European Union (EU) over a five-day period offer a seemingly infinite number of entry points for a wide range of adversaries, including Moscow – among hundreds of political parties, thousands of individual candidates, tens of thousands of voting stations and counting centers, and 400,000,000 eligible voters. Many of the individual nodes in this massive electoral process have next to no insulation against or training on how to deal with the kinds of Russian hacks we’ve seen from Washington to the Western Balkans.
Moreover, the potential political payoff from limited investment by Moscow is relatively high. European Parliament elections have historically been low-turnout affairs, especially when compared to national elections in the Member States. For example, while turnout on one end of the spectrum hovers around 90% (in Belgium, where voting is mandatory), average turnout across the Union is under 50% and is only 13% at the other end of the spectrum (in Slovakia, which regularly brings up the rear in the turnout race). Low turnout elections give extremist parties on the Left and Right (the kinds of parties with a record of support from Moscow) a disproportionate influence on the key issues being addressed in the campaign and tend to send higher numbers of anti-establishment candidates and parties to Brussels.
To Moscow’s delight, even without significant destabilizing actions from outside actors, next year’s elections are likely to deliver a European Parliament that is as fractured and dysfunctional as any that have gone before it. The mainline center-Right and center-Left (especially the Left) are under pressure across the continent for not responding to the needs of the electorate for fairness and security (perhaps rightly so, but that is not mine to judge), and it can be expected that parties that support both a weaker Union (a key Russian strategic objective) and a closer relationship with Moscow (the most important operational one) will come out at least relative victors in the incoming parliament.
So, what is to be done? First and foremost, the EU and Member States, along with all stakeholders in the election process need to start building a culture of awareness and resilience now. One interesting approach to this was on display in Brussels on the same day that the eyes of the Brussels bubble elite were trained upon Mark Zuckerberg and looking for ways to punish Facebook for its data protection problems. On that same day, IRI (along with NDI and the Defending Digital Democracy Project (D3P) at the Kennedy School’s Belfer Center and corporate partners Google and Microsoft) launched the European edition of the Campaign Cybersecurity Playbook, which is designed to make it easy for stakeholders in the coming elections to help protect themselves against the types of cyberattacks that took place in the United States in the 2016 presidential campaign.
The playbook, developed in a fully bipartisan way based on the experience of Romney 2012 campaign manager Matt Rhoades and Clinton 2016 campaign manager Robby Mook, lays out many behavioral, technological and cultural leadership steps that can be taken to help make campaigns more secure in the evolving electronic election environment. The Playbook doesn’t offer the only solution to protecting the integrity of the European Parliament (and other) elections, but it addresses the most important step, awareness of the threat. Through a culture of awareness campaigns can begin to make simple changes that are not time-, management- and cost-prohibitive to parties across the Member States.
And the need improve security among those parties is indeed great. An assessment of political party preparation for dealing with cyber threats undertaken by IRI and NDI earlier this year showed parties in a range of six countries (both Member States and Candidate Members) largely unprepared to withstand even the most basic potential attack by opponents foreign or domestic. Laptops are left unsecured in public places; passwords are set at, well, ‘password’ or shared among large numbers of staff and volunteers; and – perhaps worst of all – party leadership simply does not focus on cybersecurity as a priority and thus sends a message to staff that it just does not matter. In such circumstances, those looking to disrupt election processes sadly do not have to look far.
There is still time for measures to be put in place in a way that can help secure the process for 2019, but parties at the EU level and their national-level members need to begin now to make this so, and IRI is willing to help in any way it can, along with NDI and our partners in the private sector. Take it from us Americans, in this case, we know of what we speak. And we’d much rather share our difficult experience to help prevent those opposed to democracy from doing what they did in the US in 2016 to Europe in 2019.
If you would like to download the Cyber Playbook click HERE.

Top